What if you could instantly identify every device—even if they don’t have security agents? Beyond identifying them, imagine being able to automatically profile and classify every device, as well as gaining around-the-clock behavioral monitoring as these devices communicate across your entire network infrastructure.
 Gartner predicts the number of Internet connected devices will grow to 21-billion by 2020. The US Federal Trade Commission recently warned of the potential security and privacy risks posed by IoT devices. And Experian is predicting IoT “could usher in the next wave of large [data] breaches.” Every device on your network is a potential attack or reconnaissance point that must be secured.
Gartner predicts the number of Internet connected devices will grow to 21-billion by 2020. The US Federal Trade Commission recently warned of the potential security and privacy risks posed by IoT devices. And Experian is predicting IoT “could usher in the next wave of large [data] breaches.” Every device on your network is a potential attack or reconnaissance point that must be secured.
“IoT devices are capable of collecting, transmitting,
and sharing highly sensitive information.”
— US Federal Trade Commission
Do you know how many IoT devices are on your network? How would you know if an IoT device was compromised? IoT visibility is critical. Modern devices fall into three categories:
1. Managed Devices
Corporate-owned PCs, laptops, mobile devices and infrastructure components require management agents, allowing IT staff to discover, maintain and control them.
2. Unmanaged Devices
Employees, contractors and visitors use their own laptops, tablets and smartphones to access your network. Since you don’t own these devices, you typically have no authority to put security software (e.g. security agents) on these devices. Therefore, they are invisible to traditional security products.
3. IoT Devices
Today, the majority of the new devices connecting to enterprise networks are IoT devices. These devices can be anything from your video surveillance and audio visual systems to medical devices and 3D printers. The list goes on and on. They have purpose-built operating systems that cannot run your security software or agents. Consequently, they are simply invisible to your existing security products.
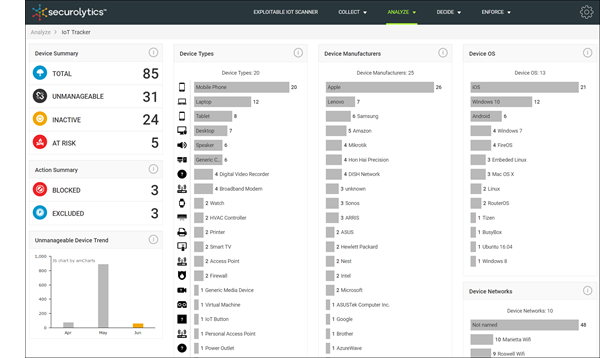
Securolytics IoT Tracker delivers complete network visibility by identifying and profiling every device. Managed, unmanaged and IoT.
![]() Securolytics IoT Tracker provides in-depth visibility through passive monitoring. We discover devices the instant they connect to your network—without requiring agents. The Securolytics ExpressForwarder™ securely COLLECTS Windows Server and network appliance logs without the need to deploy additional hardware or software. We correlate, enrich and ANALYZE data from DHCP and DNS logs to identify and profile every device and to create a baseline of normal activity. IoT Tracker then continuously monitors all devices as they communicate across your network.
Securolytics IoT Tracker provides in-depth visibility through passive monitoring. We discover devices the instant they connect to your network—without requiring agents. The Securolytics ExpressForwarder™ securely COLLECTS Windows Server and network appliance logs without the need to deploy additional hardware or software. We correlate, enrich and ANALYZE data from DHCP and DNS logs to identify and profile every device and to create a baseline of normal activity. IoT Tracker then continuously monitors all devices as they communicate across your network.
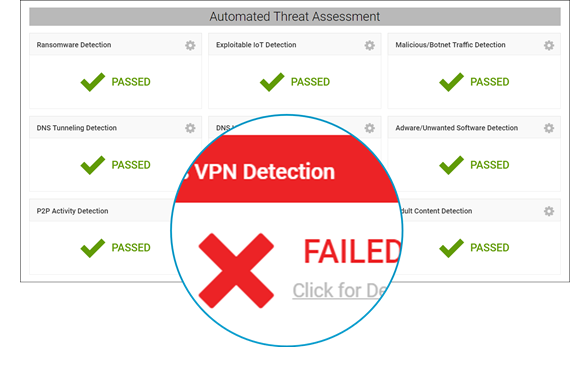 Securolytics IoT Tracker is a cloud-based threat detection and analytics tool purpose-built for the Internet of Things. We address gaps in perimeter-based defenses by identifying the symptoms of a data breach, malware infection and criminal activity through behavioral analysis and anomaly detection. And we do it all without the need to deploy additional hardware or software. Unlike traditional solutions, Securolytics uses advanced statistical modeling and machine learning to independently identify new problems, learn from what it sees, and adapt over time. We reduce the effort needed to discover IoT threats inside your network.
Securolytics IoT Tracker is a cloud-based threat detection and analytics tool purpose-built for the Internet of Things. We address gaps in perimeter-based defenses by identifying the symptoms of a data breach, malware infection and criminal activity through behavioral analysis and anomaly detection. And we do it all without the need to deploy additional hardware or software. Unlike traditional solutions, Securolytics uses advanced statistical modeling and machine learning to independently identify new problems, learn from what it sees, and adapt over time. We reduce the effort needed to discover IoT threats inside your network.
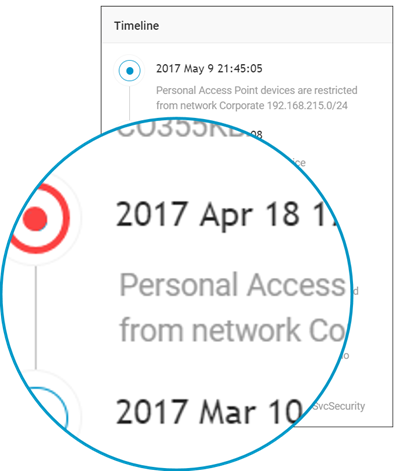 IoT Tracker continuously runs automated policy assessments across all your connected devices searching for compliance issues. The automated tests include:
IoT Tracker continuously runs automated policy assessments across all your connected devices searching for compliance issues. The automated tests include:
1. Restricted Devices
Personal access points or other devices that should not be connected to the network.
2. Restricted Operating Systems
Devices running outdated, unsupported or vulnerable Operations Systems like Microsoft Windows 95.
3. Network Hopping
Devices moving between secure corporate networks and unsecured guest networks.